Configuring Active Directory based discovery rules for Veeam Endpoint
Active Directory discovery rules allow you to discover computers being part of an AD domain.
Steven Panovski
Active Directory discovery rules allow you to discover computers being part of an AD domain.
This method is recommended for client environments with Active Directory domains of any size. Active Directory discovery rules target AD containers, which helps perform dynamic discovery: if new computers join a domain, a new run of an AD-based rule will discover these computers.
Prerequisites
Before you configure an Active Directory discovery rule:
- Deploy a master agent on a machine in the client infrastructure. The machine must be included in a domain within which computers will be discovered.
Make sure you have an account with local Administrator permissions on all computers that you want to discover.
This prerequisite is not required if you have specified a discovery account in the master agent configuration settings.
- Make sure that client computers are powered on and configured to allow discovery: the Remote Scheduled Tasks Management (RPC and RPC-EPMAP) firewall rules must allow inbound traffic.
- On client computers that run a Windows desktop OS, the Windows Management Instrumentation (WMI-In) firewall rule must be configured allow inbound traffic.
- If you plan to install Veeam backup agents as part of the discovery procedure, make sure that client computers are configured to allow installation: the File and Printer Sharing (SMB-In) firewall rule must allow inbound traffic.
If you plan to assign a backup policy as part of the discovery procedure, create a new backup policy or check and if necessary customize one of the predefined policies.
Configuring Active Directory Discovery Rule
To configure an Active Directory discovery rule:
- Log in to Veeam Service Provider Console.
- In the menu on the left, click Discovery.
- On the Rules tab, click New.
Veeam Service Provider Console will launch the New Rule wizard.
4.At the Rule Name step of the wizard, specify a discovery rule name.
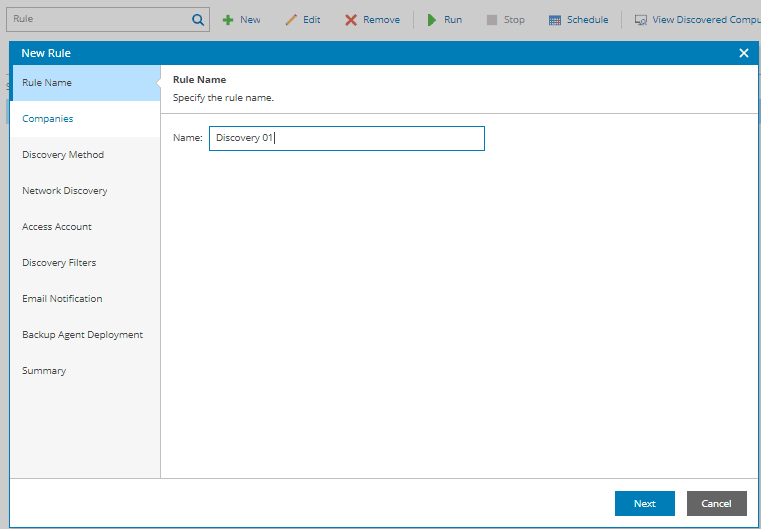
- At the Companies step of the wizard, choose one or more companies for which the discovery rule is configured. Use the search field at the top of the list to find the necessary companies.
You can select more than one company at this step. In this case, after you complete the wizard steps, Veeam Service Provider Console will create a separate discovery rule for each company.
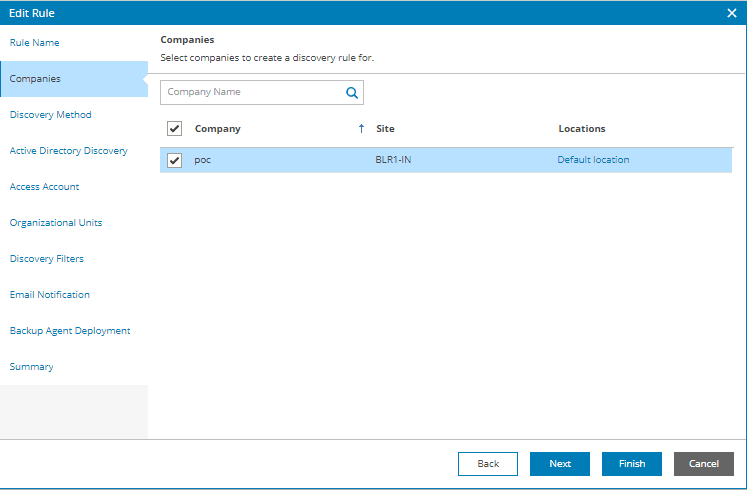
- Click a link in the Locations column, then click a link in the Master Agent column, and select a management agent that will be used as the master agent for discovery in each company location.
By default, discovery is performed in all company locations where you deployed a master agent. If you choose to perform discovery in multiple locations, after you complete the wizard steps, Veeam Service Provider Console will create a separate discovery rule for each location. If you do not want to perform discovery in some company locations, clear check boxes next to these locations.
7.At the Discovery Method step of the wizard, select Microsoft Active Directory discovery.
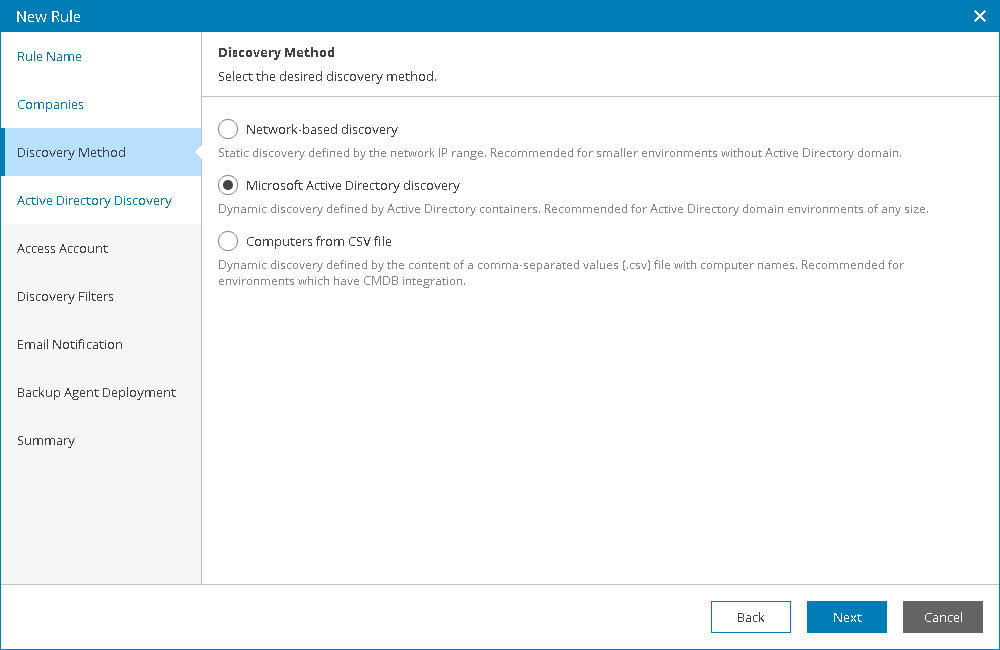
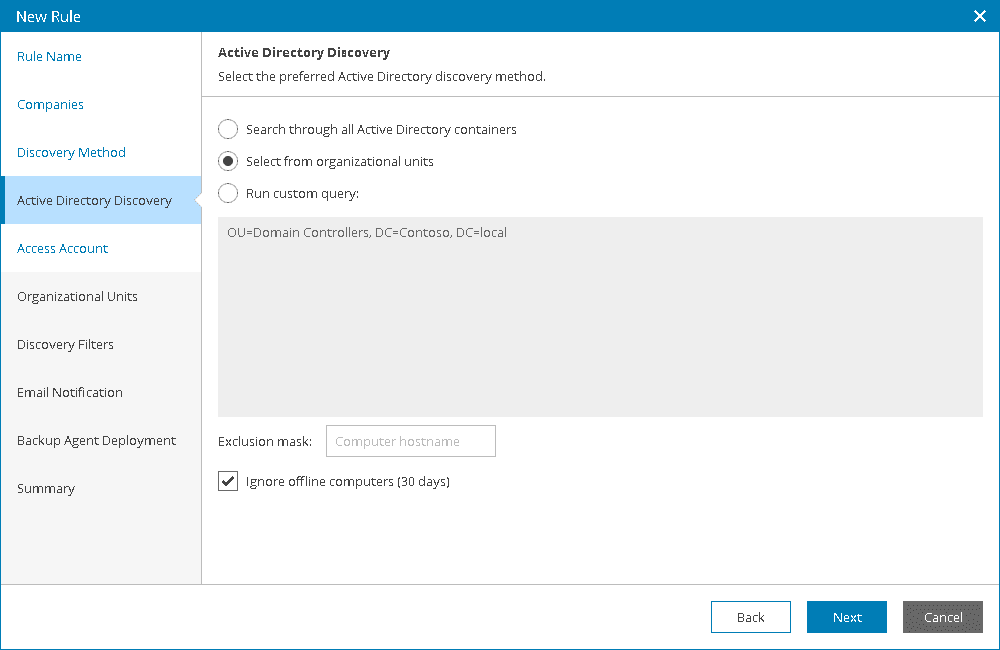
- At the Active Directory Discovery step of the wizard, select the necessary method for Active Directory discovery:
- Select Search through all Active Directory containers to discover all computers that are included in the Domain Controllers and Computers organizational units.
- Select Select from organizational units to discover computers that are included in selected organizational units only.
If this option is selected, the Organizational Units step will become available in the wizard.
- Select Run custom query to discover computers based on results of a custom query. In the text field at the bottom, specify a LDAP query that must return a list of computers to scan.
In the Exclusion mask field, specify a mask for names of computers that must be excluded from discovery. The mask can contain an asterisk (*) that stands for zero or more characters. You can specify multiple masks separated with commas.
Select the Ignore offline computers check box to exclude from discovery computers that did not contact a domain controlled for 30 days or longer.
- At the Access Account step of the wizard, specify credentials of an account that the master agent will use to connect to computers within the discovery scope. The account must have local Administrator permissions on all discovered computers.
If you have specified a discovery account in the master agent configuration settings, select the Use credentials specified in the master agent configuration check box. For details on specifying master agent configuration settings.
Credentials specified in the master agent configuration take precedence over credentials specified in the discovery rule. For discovery, the master agent will use an account specified in its configuration settings. In case this account is not valid or not set, the master agent will use an account specified in the discovery rule.
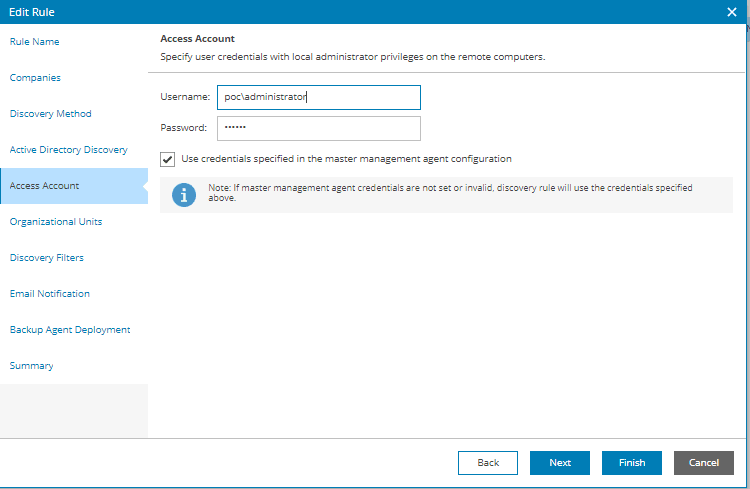
- At the Organizational Units step of the wizard, select organizational units that must be scanned for discovered computers.
This step of the wizard is available if at the Active Directory Discovery step you have selected the Select from organizational units option.
- Click a link in the Locations column for the necessary company.
- In the Locations window, click an organizational unit link for the necessary company location.
- In the Organizational Units window, select check boxes next to units that must be included to the discovery scope.
If you want to include a folder and all underlying subfolders to the discovery scope, right-click the check box and click Select all..
- In the Organizational Units window, click OK.
- In the Locations window, click OK.
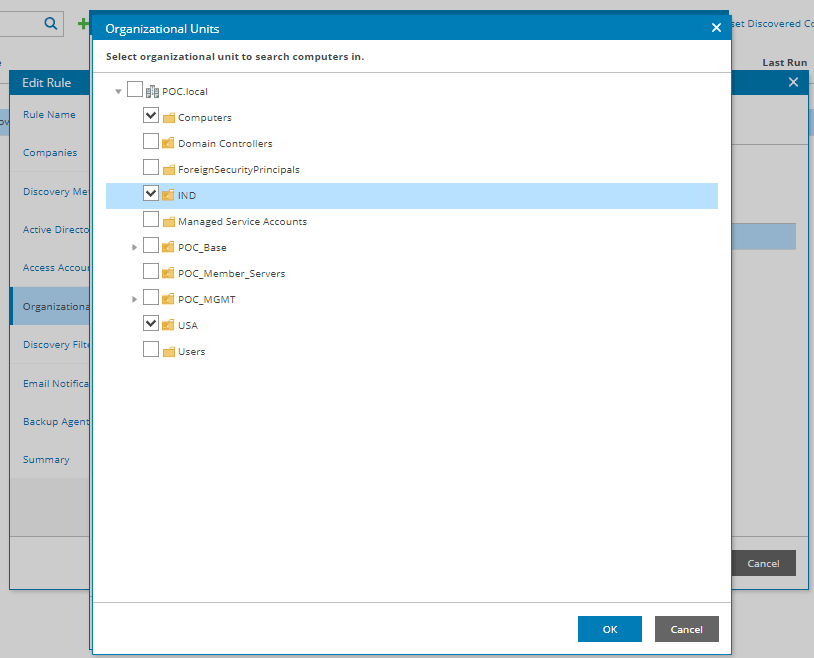
- At the Discovery Filters step of the wizard, choose what filters you want to enable for discovery.
- To filter computers by OS type, select By OS type in the list and click Edit. In the Operating System window, select the type of OS that must run on discovered computers (Server operating system, Client operating system). Click OK.
- To filter computers by application, select By application in the list and click Edit. In the Application window, select applications that must run on discovered computers (Microsoft Exchange Server, Microsoft SQL Server, Microsoft Active Directory, Microsoft SharePoint, Oracle, and Other Applications). Click OK.
- To filter computers by platform, select By platform in the list and click Edit. In the Platform window, select platforms on which discovered computers must run (Microsoft Hyper-V and VMware vSphere, Physical computers, Microsoft Azure, Amazon Web Services, Other). Click OK.
- If you want to perform discovery among accessible computers only, select the Do not show inaccessible computers check box.
NOTE
Different types of filter conditions are joined using Boolean AND operator. For example, if you enable filters Server operating system, Microsoft SQL Server and VMware vSphere, the list of discovered computers will include only VMware vSphere VMs that run Windows Server OS and Microsoft SQL Server.
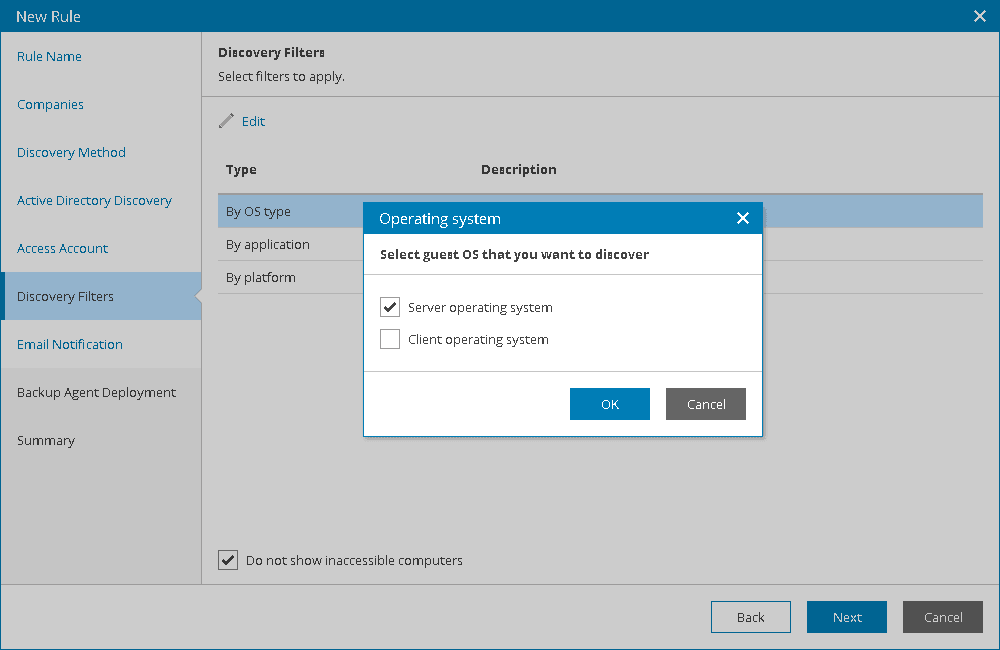
- At the Email Notification step of the wizard, you can enable notifications about discovery results by email.
- Select the Send notifications check box and specify a schedule according to which email notifications must be sent.
- In the Subject field, specify the subject of the notification.
- In the To field, specify an email address at which the email notification must be sent.
- Select the Send notification email after the first run check box if a notification about discovery results must be sent after the first run of the discovery rule, regardless of the specified schedule.
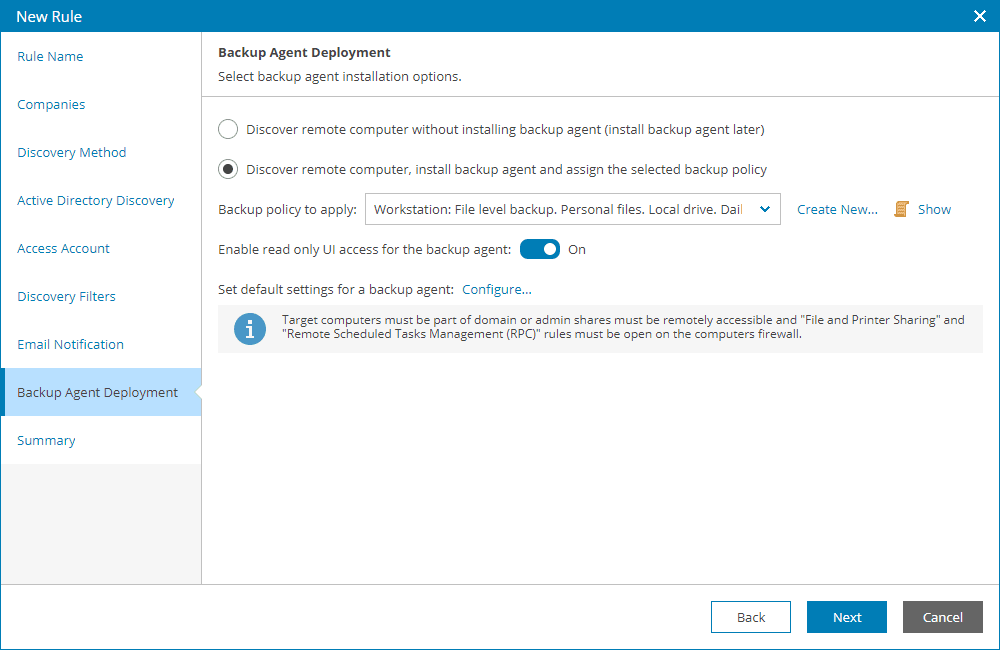
- At the Backup Agent Deployment step of the wizard, specify whether you want to install Veeam backup agents on discovered computers:
- If you do not want to install Veeam backup agents as part of the discovery process, leave the Discover remote computer without installing backup agent option selected.
- If after discovery Veeam backup agents must be installed automatically, select the Discover remote computer, install backup agent and assign the selected backup policy option.
From the Backup policy to apply list, choose a backup policy that must be assigned immediately after installation. To view the selected policy details, click the Show link. If you do not want to assign any backup policy after installation, choose No policy from the list.
If you do not have the necessary backup policy configured yet, you can click the Create New link to create a new policy, without exiting the New Rule wizard. For details on backup policies
By default, the read-only access mode is enabled for all Veeam backup agents installed as part of discovery. To disable the read-only access mode for Veeam backup agents on discovered computers, set the Enable read only UI access for the backup agent toggle to off.
For details on the read-only access mode for Veeam backup agents To push global settings for Veeam backup agents, click Configure and specify default global settings for Veeam backup agents.
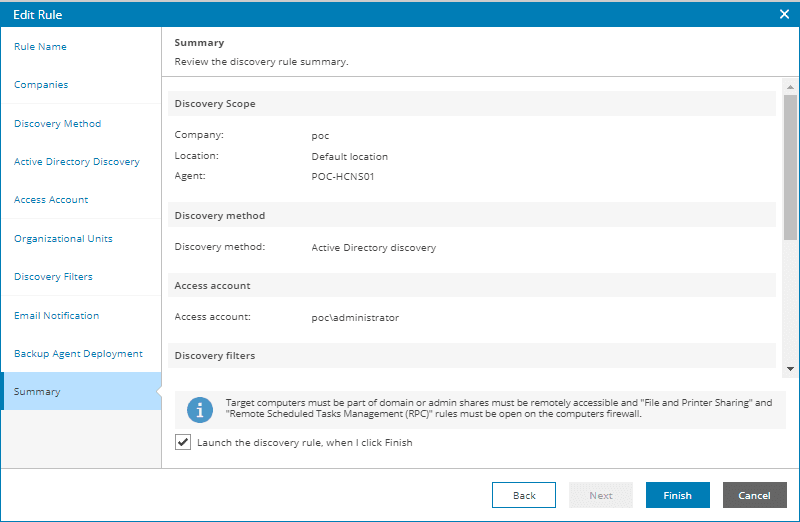
- At the Summary step of the wizard, review discovery rule settings.
- To start discovery after you save the rule, select the Launch the discovery rule when I click Finish check box.
If you do not select this check box, you will need to launch discovery later.
Click Finish.
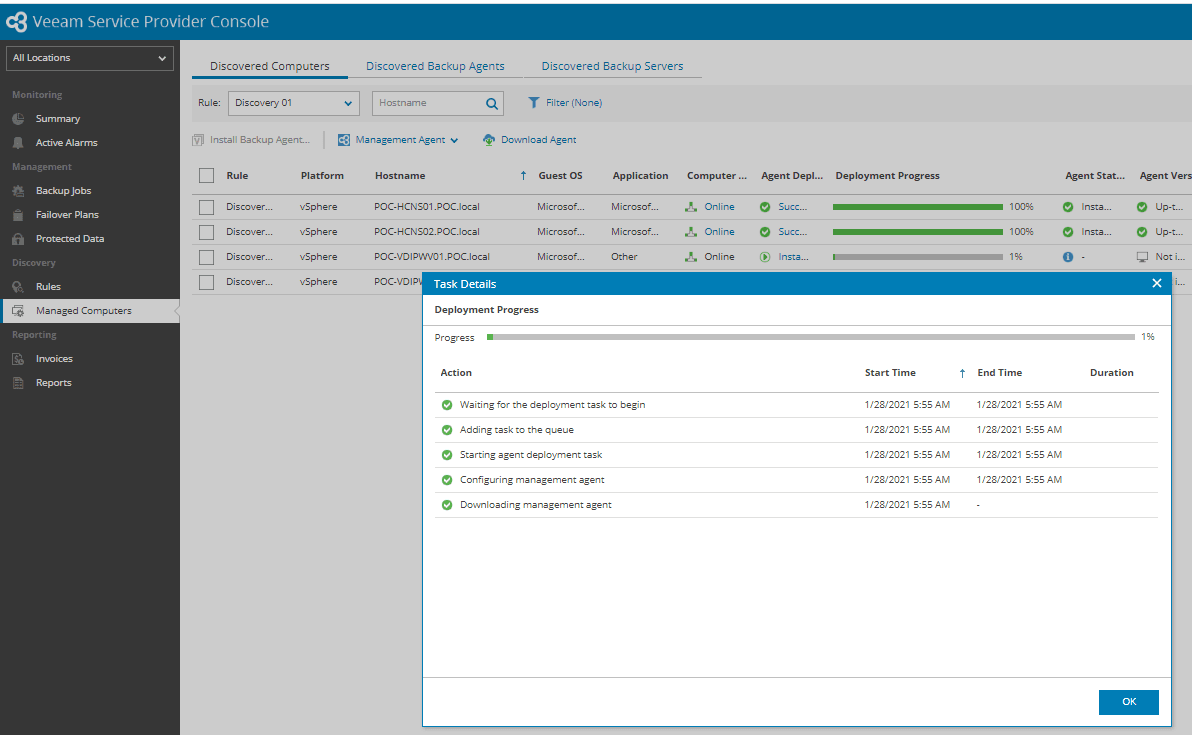
Once discovery rule completed, Management agent and Backup agent deployment will completed as per defined policy. All status are viewable in Managed Computer menu in VSPC Portal.
Related Posts
All posts

Three Critical Issues in Cybersecurity for March 2026
This month we look at three issues: • Agentic AI and the problems it presents • Possible threats from online add-ons to familiar platforms • The skill gap in cybersecurity

How Grandpa Internet’s OpenStack Migration Effort Proved a Win for UBX Clients
We needed a solution, and we sicced Grandpa Internet himself – our own Reynaldo Martinez – on the problem.

Team Member Profile: Richard Dulcey
Caracas, Venezuela native Richard Dulcey has been working in the IT field for the past 20 years – exclusively in South America. A specialist in Linux engineering, Richard was working and living in Argentina in 2024 when a longtime colleague and friend named Reynaldo Martinez shared the positive experience he was having working remotely for UBX Cloud.